A DNSBL, also known as DNS Black Lists or DNS Block Lists or RBL (Real-time Blackhole List), are often used in mail servers in combination of content filters to fight incoming spam. Some have been around for a very long time (kudos to Spamcop and Spamhaus!), some have disappeared over the years.
How a DNSBL works
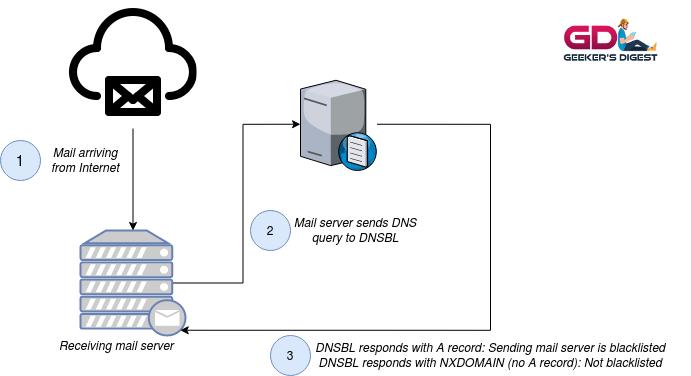
A DNSBL works kind of similar to a public DNS resolver. But instead of resolving a public domain, the (reversed) IP address is checked in the blocklist's database. If the IP address is in fact listed in the blocklist, the DNSBL responds with "127.0.0.2" as a DNS A record. If the IP address is not listed, the DNSBL will return a NXDOMAIN response.
Depending on the DNSBL, multiple responses may indicate a different kind of blacklisting of the requested IP address.
In the following example, the IP of Geeker's Digest is taken and checked on the Spamcop DNSBL:
ck@linux ~ $ dig 210.71.103.212.bl.spamcop.net +short
ck@linux ~ $ There was no A record returned on this DNS query (NXDOMAIN). This means: This IP address is not blacklisted. Hurray!
Now let's do this with an IP address of an already blacklisted mail server:
ck@linux ~ $ dig 221.64.129.23.bl.spamcop.net +short
127.0.0.2Oh, we got a winner! The IP address 23.129.64.221 is blacklisted in Spamcop's DNSBL!
How to use a DNSBL on your mail server
Well documented DNSBLs usually describe how their service can be implemented in a mail server. In Postfix, one of the most installed mail servers on Linux, a DNSBL is typically configured using the smtpd_client_restrictions option. The following example uses a couple of DNSBLs:
smtpd_client_restrictions = permit_mynetworks,
permit_sasl_authenticated,
reject_rbl_client bl.spamcop.net,
reject_rbl_client zen.spamhaus.org,
reject_rbl_client b.barracudacentral.org,
reject_rbl_client ix.dnsbl.manitu.net,
reject_rbl_client psbl.surriel.comWhen such a blacklisted mail server tries to send an e-mail, the e-mail will be rejected by the receiving server with an error message like this:
Feb 3 23:03:43 mail01 postfix/smtpd[26189]: NOQUEUE: reject: RCPT from unknown[23.129.64.221]: 554 5.7.1 Service unavailable; Client host [23.129.64.221] blocked using bl.spamcop.net; Blocked - see https://www.spamcop.net/bl.shtml?23.129.64.221; from=<[email protected]> to=<[email protected]> proto=SMTP helo=<hotmail.com>How to monitor if your own mail server got blacklisted
If you run your own mail server or you manage mail servers with a lot of mail accounts, you want to make sure, your server did not land on a blacklist. There are a couple of domains, where a mail server IP or domain can be entered manually and multiple DNSBLs will be checked. BlacklistAlert.org is such an example.
But you want to have the blacklist monitoring automated so this is where the monitoring plugin check_rbl from Matteo Corti comes into play. It supports a big list of blacklists (currently 90 active lists as of this writing) and is regularly updated. The plugin goes through the whole list of (user-) defined blacklists and if your server was found anywhere, the plugin will alert.
If you are running a classic systems monitoring tool, such as Nagios, Icinga, checkmk, Naemon or others, the plugin can be easily integrated into it.
To check a single DNSBL, use the -s parameter followed by the blacklist domain:
ck@linux ~ $ ./check_rbl -H 212.103.71.210 -s bl.spamcop.net
CHECK_RBL OK - 212.103.71.210 BLACKLISTED on 0 servers of 1 - Additional checks on http://www.blacklistalert.org/?q=212.103.71.210 | servers=0;0;0 time=0s;;To use a list of blacklists, use the check_rbl.ini file from the plugin's repository and refer to it with the –extra-opts parameter. As this takes quite some time, the default plugin timeout of 15 seconds won't be enough. Increase the timeout with the -t parameter so the plugin has enough time to query all the blacklists from the ini file:
ck@linux ~ $ ./check_rbl -H 212.103.71.210 --extra-opts="rbl@/usr/lib/nagios/plugins/rbl.ini" -t 120
CHECK_RBL OK - (4 servers timed out: dyna.spamrats.com, noptr.spamrats.com, spam.spamrats.com, dnsbl.anticaptcha.net) - Additional checks on http://www.blacklistalert.org/?q=212.103.71.210 | servers=0;0;0 time=15s;;The plugin returned "CHECK_RBL OK", which means the given IP address was not blacklisted. 4 blacklists timed out and did not respond within the required time. This could mean that these DNSBL are temporarily offline or suffer from perfomance issues, or that they were decommissioned.