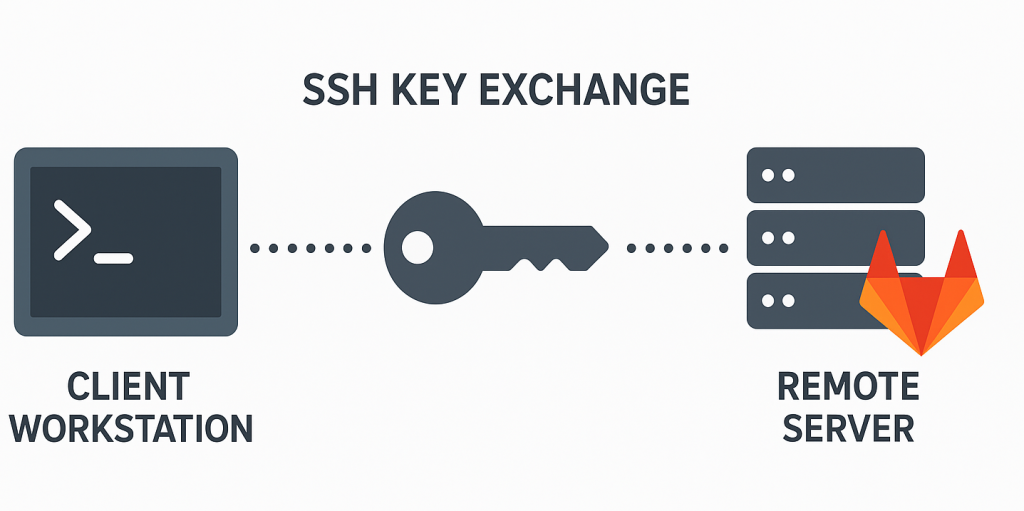
In order to communicate (and authenticate) with Git repositories on GitLab, there are a couple of possibilities. One such possibility is by using SSH keys – similar as if you would connect to a remote server using SSH.
GitLab notifies: Your SSH key is expiring soon
Access to Git repositories need proper authentication. And because security is important, access tokens or SSH keys expire after a certain time – that's a default setting in all newer GitLab releases.
SSH keys expire?
No, SSH keys do not expire. You create your personal SSH key (using ssh-keygen or a similar method) and you can use the key as long as it's compatible with the target SSH server. But in this context, the "entry" of your public SSH key in GitLab expires.
If correctly configured, GitLab automatically sends a notification to affected users:
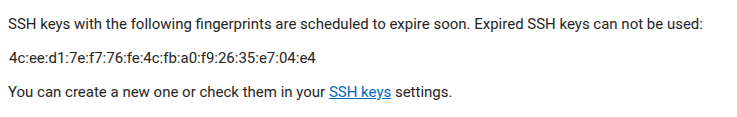
The e-mail shows the "fingerprint" of the affected SSH key.
How to find the fingerprint of your public SSH key
When you create a new SSH key on your Linux (or macOS, BSD or other Unix based) machine you receive the fingerprint in the output. Of course this output is rarely saved. But with the ssh-keygen command you can see this fingerprint again on your public key:
ck@linux ~ $ ssh-keygen -lf ~/.ssh/id_rsa.pub | head -n 1
2048 SHA256:33SN8e//9nCvCU5Re3srTl5fCAr8E30gczExJlfgsqw mysshkey (RSA)"But this does not look at all like the fingerprint shown in the GitLab e-mail. The format is completely different!"
Yes, you're absolutely right. The fingerprint (by default) is shown as a SHA256 hash.
GitLab however uses an MD5 hash of the stored public SSH key. We need to tell ssh-keygen to use the MD5 hash instead:
ck@linux ~ $ ssh-keygen -E md5 -lf ~/.ssh/id_rsa.pub | head -n 1
2048 MD5:bd:38:a5:9b:76:d5:9e:81:b9:ea:3a:f5:4f:4d:0a:07 mysshkey (RSA)But that's still not the fingerprint shown in the GitLab e-mail. Maybe another public key was used on the GitLab account? Let's check the newer ED25519 public key:
ck@linux ~ $ ssh-keygen -E md5 -lf ~/.ssh/id_ed25519.pub | head -n 1
256 MD5:4c:ee:d1:7e:f7:76:fe:4c:fb:a0:f9:26:35:e7:04:e4 mysshkey (ED25519)And here it is! The MD5 fingerprint of this public key (id_ed25519.pub) now matches the one stored in the GitLab account.
Quickly retrieve all fingerprints of all local public keys
With the following one-liner you can quickly identify the MD5 fingerprints of all your public ssh keys, ending with the suffix .pub inside your ~/.ssh directory:
ck@linux ~ $ for pubkey in $(ls ~/.ssh/*.pub); do fp=$(ssh-keygen -E md5 -lf ${pubkey} | head -n 1); echo "${pubkey}: ${fp}"; done
/home/ck/.ssh/id_ed25519_additional.pub: 256 MD5:fb:83:02:70:a1:69:e8:db:28:56:6b:39:33:1e:b7:de myothersshkey (ED25519)
/home/ck/.ssh/id_ed25519.pub: 256 MD5:4c:ee:d1:7e:f7:76:fe:4c:fb:a0:f9:26:35:e7:04:e4 mysshkey (ED25519)
/home/ck/.ssh/id_rsa.pub: 2048 MD5:bd:38:a5:9b:76:d5:9e:81:b9:ea:3a:f5:4f:4d:0a:07 mysshkey (RSA)